In 1989, long before the widespread adoption of the internet, cyber criminals were using floppy disks to spread ransomware across computers. Today’s cyber criminals have evolved their approach using advanced strains of ransomware that encrypt data on an organization’s network or lock users out of their devices. These hackers then demand a ransom, typically in the form of Bitcoin, before restoring the data back to normal.
Ransomware is a legitimate threat, with estimates from the U.S. Department of Justice showing that over 4,000 of these attacks have occurred every day since the beginning of the year.
In a recent industry report by BitSight, researchers analyzed the growing trend of ransomware across nearly 20,000 companies to identify common forms of ransomware, and identify which industries are most susceptible to these types of attacks. This slideshow highlights the findings of this recent report.
The Rise of Ransomware
Click through for findings from an industry report on ransomware, conducted by BitSight.
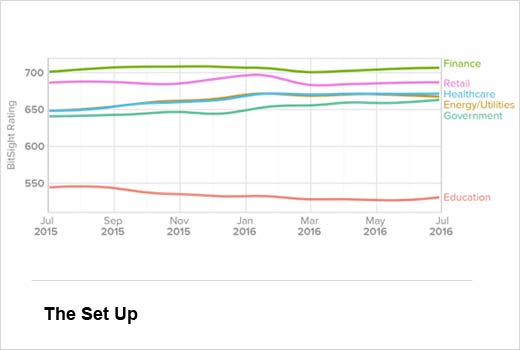
The Set Up
As part of this report, data scientists examined the cybersecurity performance of nearly 20,000 companies. The findings highlight the security posture of different industries over the last 12 months and the growth of ransomware during that time. Before examining ransomware, researchers explored the cybersecurity posture of six major industries: government, health care, finance, retail, education and energy/utilities. Findings revealed that certain industries have seen a steady increase in their ratings, while others have worsened
The security ratings range from 250 to 900, with higher ratings indicating better security postures. Findings revealed that certain industries have seen a steady increase in their ratings, while others have worsened.
Ransomware Gaining Traction
The rate of ransomware has significantly increased for every industry examined over the last 12 months. Cyber criminals are making a lucrative business through ransomware attacks. Hospitals, in particular, may pay a ransom because their patient data is critical in life-or-death situations. This was the case with Hollywood Presbyterian Medical Center earlier this year, which chose to pay a $17,000 ransom to hackers who had locked some of the hospital’s critical data. MedStar Health, another medical center, reported earlier this year that malware had caused a shutdown of some systems at its hospitals in Baltimore. Methodist Hospital in Henderson, Kentucky even declared an internal state of emergency after its systems were attacked by a strain of ransomware known as Locky.
Education Has Highest Rate of Ransomware
Education has the highest rate of ransomware of all industries examined. In fact, these institutions have over three times the rate of ransomware found in health care and more than 10 times the rate found in finance. With access to social security numbers, medical records, intellectual property, research, and financial data of faculty, staff and students, these institutions are a prime target for cyber attacks.
Government’s Ransomware Dilemma
Of the six industries examined, government had the second-highest rate of ransomware. In fact, ransomware in this sector more than tripled over the last 12 months. Sixty-seven different government organizations (e.g., law enforcement groups, federal agencies, etc.) had ransomware on their corporate networks over the past 12 months.
Ransomware Continues to Rapidly Evolve
Most ransomware attacks share a common trait — they begin with one seemingly benign email attachment opened by an employee. This action introduces malicious code into the network that encrypts or locks critical data (e.g., patient records, financial information or business documents). One in ten organizations in education has been impacted by Nymaim, while 34 different government groups have been hit with Locky — which was discovered less than eight months ago — and has already become the second-most common type of ransomware found across the six industries examined. Nymaim, although typically associated with ransomware, is actually a Trojan that can be used to install a variety of malware. Similarly, Matsnu is another type of Trojan malware that can remotely download and execute files. One unique capability of Matsnu is its ability to lock or unlock computers for ransom.
Pay the Ransom or Not?
Organizations need to understand the risks associated with ransomware and weigh their options accordingly to determine which approach is the best one to take. However, experts suggest that paying the ransom in these attacks does not help. According to FBI Cyber Division Assistant Director, James Trainor, “paying a ransom not only emboldens current cyber criminals to target more organizations, it also offers an incentive for other criminals to get involved in this type of illegal activity.” While the FBI does not support paying a ransom, it does recognize that executives, when faced with interoperability issues, will evaluate all options to protect their shareholders, employees and customers.