We’ve been taking a look at passwords and feasible replacements for them in authentication systems here at IT Business Edge. One key to the equation of letting go of our reliance on an obsolete and weak system of passwords for access is user acceptance of new security methods. Change is hard.
Some signals from the market indicate that users are coming to terms with the idea that they’ll indeed have to make some changes in order to support efforts to protect their data privacy and system security. In a recent Telstra survey of over 4,000 financial services consumers, a quarter of respondents said they would be willing to share their DNA information with a financial service provider for use in authentication. That’s a pretty strong indicator.
But when Sue Marquette Poremba talked to several security experts about what comes after passwords, many of them expressed skepticism that users will be as flexible as they think they can be. “Whenever we introduce barriers to logging into devices, or making payments, then the user becomes frustrated,” says Phillip Dunkelberger, president and CEO at Nok Nok Labs.
Perhaps the method of introduction will have to be altered to sidestep frustrations and the potential of lost customers and business. And, of course, all scenarios are not created equal.
“The complication is finding the right balance between convenience for users and the right level of security for the information being protected,” said Travis Greene, identity and access management solutions strategist at NetIQ. “Imagine a health care professional struggling to access life-saving, but regulated information. Risk-based authentication techniques, which require the minimal level of authentication for the situation, hold promise. But if a user is in a work environment during business hours, authenticate once and provide single-sign on to all low-risk information.”
Prudent providers are moving into some very small tests to see how users respond to change: Carl Weinschenk describes a 500-user test at MasterCard in which subjects will use facial scans and fingerprints instead of passwords, for example. In contrast, Microsoft’s use of biometric access in the new Windows 10 operating system, while it has the potential to instantly reach many more users, carries the burdens of higher costs for better cameras, plus potentially irritating physical requirements for users.
The results of a new survey by Accenture may carry good news for both end users and providers working to maximize their data security and minimize their reliance on passwords. And the number of respondents is quite impressive: 24,000 people in 24 countries.
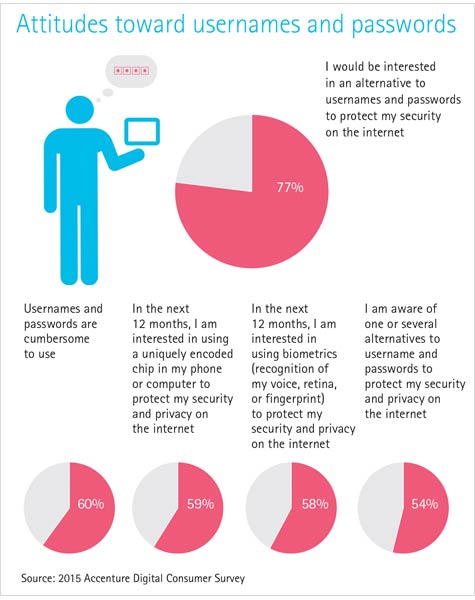
The 2015 Accenture Digital Consumer Survey was conducted in countries including the U.S., Canada, India, Japan, Mexico, Russia and Saudi Arabia, and kept the numbers proportional to the online population in each country.
The summary, “Digital Trust in the IoT Era,” which goes far beyond Internet of Things issues, found that 60 percent of respondents find usernames/passwords “cumbersome,” and 77 percent said they were interested in using alternatives to protect their security. Respondents in China and India were most open to these alternatives, at 92 and 84 percent, respectively.
Overall, 46 percent of respondents said they are confident in the security of their personal data – a number I frankly find surprisingly high.
However, said Robin Murdoch, managing director of Accenture’s Internet and Social business segment, in a statement:
“Digital trust concerns are not limited to one type of country or part of the world. In developed and emerging countries, consumer wariness about data privacy and digital trust is intensifying as the exploding Internet of Things market generates unprecedented amounts of consumer data on more devices. Companies that build the most trust with consumers will be able to access more consumer data, use analytics to unlock more value from that data, and offer more revenue-generating services and applications leveraging Internet of Things opportunities.”
Will Internet of Things applications be the factor that pushes businesses and end users past their reliance on outdated passwords?
Kachina Shaw is managing editor for IT Business Edge and has been writing and editing about IT and the business for 15 years. She writes about IT careers, management, technology trends and managing risk. Follow Kachina on Twitter @Kachina and on Google+